Filtering domain joined users was straightforward to configure.
What I have done to accept a certain user group for VPN was,
- Create a security group for VPN users in AD
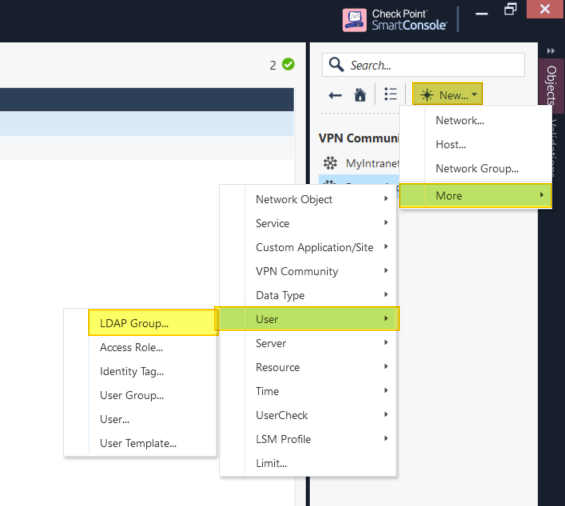
- Create LDAP Group from Checkpoint SmartConsole
- Fill in desired information, I selected Only Group in branch (DN prefix) option from Group's Scope section and added AD group created above.
- Add the LDAP group created above to RemoteAccess group under VPN Communities.
Now you have user control to accept VPN connection. What you need to do is add required users in AD group you created. Problem is users can install Checkpoint VPN client to their personal computers which may contain nasty virus/malware. Providing right user credential will be accepted from any computers. Therefore we need computer control to accept VPN connection.
Googling gave me brief ideas but not exactly what I wanted. Especially dealing with computer name was the worst scenario as user can change their computer name to one of domain joined computers. I tested and it was accepted.
Well my method is not 100% secured as users can change this registry value on their personal computer but I hope no one wicked in the organization and believe this is slightly more secured than dealing with computer name. I found a couple of registry key value of joined domain from,
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\DomainHKEY_CURRENT_USER\Volatile Environment\USERDNSDOMAINI chose a registry value from Volatile Environment. This registry value will be used for compliance.
Now we need to edit SCV(Secure Configuration Verification) to set a policy which will be applied before establishing the connection.
Here are the steps,
- open SSH connection to the server which has Network Policy Management Blade
- Go to expert mode
- open up local.scv file using vi
- vi $FWDIR/conf/local.scv
- Scroll down and find the section starting with : (RegMonitor
- Press Insert key to go into edit mode and edit as required.
: (RegMonitor
:type (plugin) :parameters ( :string ("HKEY_CURRENT_USER\Volatile Environment\USERDNSDOMAIN=your domain name here") :begin_admin (admin) :send_log (alert) :mismatchmessage ("Access Denied: Please contact your system administrator.") :end (admin) ) )
- And enable RegMonitor policy by adding the policy name. It's nearly at the bottom of file.
:SCVPolicy (
: (RegMonitor)
)- Now press ESC key to exit edit mode and type :x to save
- Open SmartConsole and Publish and Install Policy. Make sure Desktop Security is selected.
It will check the registry key value every time user attempts to connect VPN connection. You can add your own error code under mismatchmessage for easy debugging if you want.
Now we check user name from AD group and domain joined computer for secured VPN connection,














COMMENTS